The growing threat against backups by cybercriminals in the course of an attack has the industry looking for a stronger definition of what should be included when considering where and how your backups are stored.
The identification and destruction of backups has long been a known threat tactic used as part of ransomware attacks, with the obvious logic being, “If you don’t have backups, you have no choice but to pay the ransom.” What started as simple scripts designed to find specific file types has evolved. In some cases, the search for backups is rendered as a complex sub-attack that uses known vulnerabilities to gain access to SAN and NAS devices before finding and deleting backup files. In other cases, it’s attacks specific to a backup vendor designed to find user accounts with application-specific privileges to eliminate relevant backups via APIs.
Threat actors aren’t fools; they understand the mitigation steps taken by today’s brightest IT organizations and look for ways to circumvent security controls to locate, exfiltrate, and delete backups to leave the victim organization with paying the ransom as their only option.
But the good guys have been diligently evolving as well. Last year, Gartner put out the Hype Cycle for Storage and Data Protection Technologies, 2022, coining a since-repeated phrase that denotes having backup storage that is resilient to cyberattack: cyberstorage.
According to Gartner, cyberstorage “protects storage system data against ransomware attacks through early detection and blocking of attacks, and aids in recovery through analytics to pinpoint when an attack started. The solutions can be pure software, a dedicated appliance or fully integrated with the data storage solution.”
In short, Gartner says, “Cyberstorage provides active defense against cyberattack on unstructured data.” They paint a picture of the technology timeline in the Hype Cycle shown below:
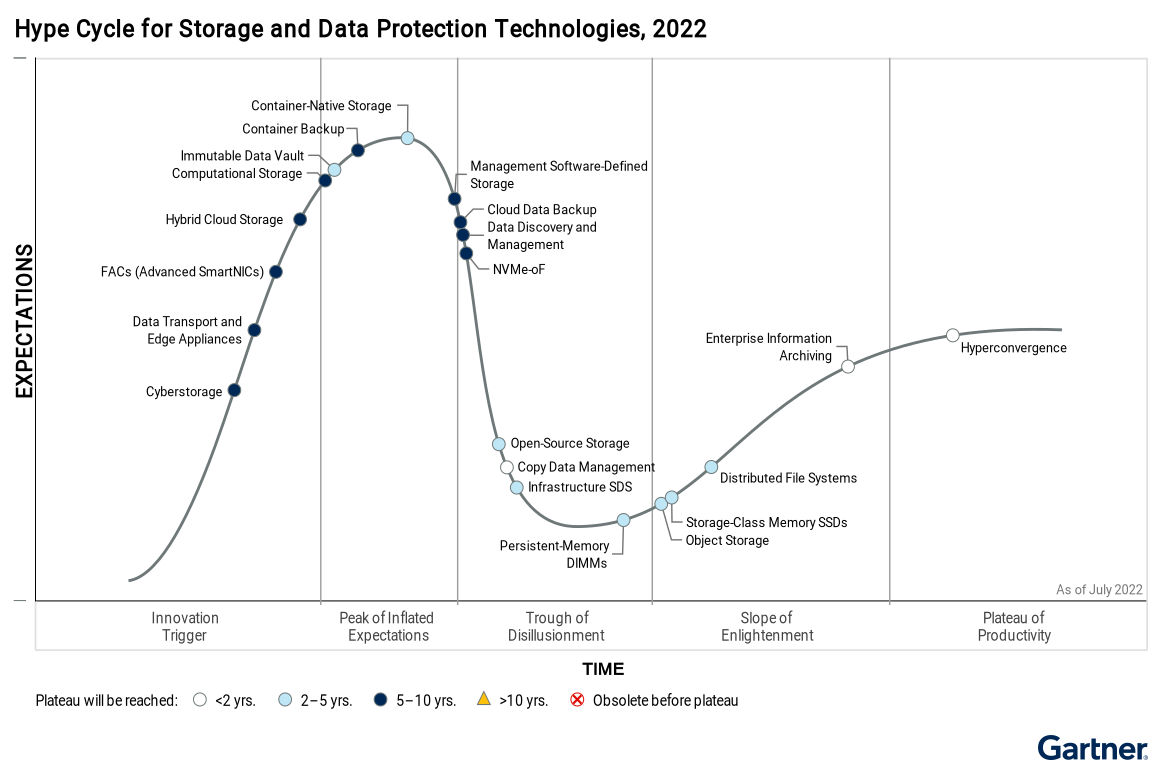
And while the Hype Cycle report is looking for storage-vendor specific solutions that may take as many as 10 years to come to fruition, as with any cybersecurity need, there are many ways to achieve the same end goal – and in a much shorter period than 10 years!

Let’s break cyberstorage down into a few specific goals to help find ways to achieve cyberstorage practically while the industry attempts to catch up and create some form of a unified solution:
1) Early Detection and Blocking of Attacks – I believe that Gartner has it in mind that this “detection” and “blocking” is done as part of the storage system. But the preventative and protective layers of your cybersecurity strategy should be most effective well before an attacker ever gets to the point where they are trying to encrypt or delete backups, right?
Most cybersecurity practitioners put the emphasis on the most common initial attack vector of most ransomware attacks – phishing – putting a layered strategy in place to keep malicious email from ever reaching an inbox. But a bit more than 1 in 9 attacks actually see the inside of an inbox – making it critical that your “early detection and blocking” of attacks includes endpoint protection that stops both known and unknown threats.
And by “endpoint”, I don’t just mean workstations and laptops; I mean every system on the network. Part of Gartner’s definition of cyberstorage includes pinpointing when an attack started, so that meaningful recovery actions can be taken that won’t include infected systems and data within the backups used. This means your endpoint protection needs to be on any system that can be used as an asset for the attacker. Additionally, it must provide an ability to detect malicious or suspicious code, regardless of the obfuscation method(s) used and whether the code is run or lies dormant. The goal here is to find the malicious code before it does any harm.
2) Keeping Backups Inaccessible to Attackers Through Cloud and Hybrid-Cloud Storage – According to the Gartner report, by 2026 “large enterprises will triple their unstructured data capacity stored as file or object storage on-premises, at the edge or in the public cloud, compared to 2022.” Note that on-prem is still mentioned here. The somewhat old, but still pretty relevant, “3-2-1 Backup Rule” states that there should be one copy (the “1” in “3-2-1”) of the data held offsite. This is generally held today to mean stored in the cloud.
Given that attackers are seeking out backups as part of ransomware attacks, it makes sense that organizations should take steps to ensure there is a copy of backups that is seemingly out of reach of an attacker by keeping it off-premises (with the cloud being the obvious choice). Of course, I’m assuming that you’re using a modern backup solution that supports cloud-based backups.
3) Making Backups Immutable – There’s an extension to the “3-2-1 Backup Rule” that states that one of your copies should be immutable (that is, it can’t be modified or deleted). The term “Immutable Data Vault” can also be found in Gartner’s Hype Curve above, demonstrating that this additional security measure – while not the ultimate answer to stopping attacks – plays a role in achieving a state of cyberstorage. (It’s likely – from Gartner’s perspective – that this technology will simply become a feature in a much larger “secure storage” offering in the future. But, for now, it’s a capability offered by many cloud storage providers today that you can take advantage of.)
Why Attempt to Achieve Cyberstorage?
If you’ve been in IT for a while, you know that Gartner doesn’t always get their industry trending right. But this cyberstorage concept just makes sense. While cybercriminals have been changing their ransomware tactics to increase the pressure to pay a ransom, the “get out of jail free” card has always been – and will continue to be – the presence of viable, undisturbed backups that can recover an environment quickly.
But beyond ransomware attacks specifically, additional benefits also exist. Endpoint protection based on deep learning can help to stop every kind of cyberattack and not just those that seek to delete your backups and encrypt your data. Cloud-based backups increase the recovery options from just on-prem to also include a cloud-based virtual environment. Immutable backups imply a high data durability standard – meaning you can rely on the backed-up data when it comes time to recover.
By rethinking your storage strategy to one that is focused on Gartner’s definition of cyberstorage, it’s possible to achieve a simple but effective version that more effectively and efficiently protects the organization against any kind of threat that may disrupt the business, including ransomware.







