Some EU customers don’t just ask where data is stored. They ask who can operate the cloud environment, how access is governed, and what happens under regulatory pressure.
Master Password Feature Improvement in MSP360 Backup 6.1.1
MSP360 Backup 6.1.1 is equipped with the improved master password feature.
With a master password feature enabled, all storage credentials, backup and restore plan configurations, settings are encrypted and secured with a signature. Any unauthorized actions will require to provide the master password.
The feature provides the following improvements:
- Command Line Interface is now can be protected with a master password
- Unauthorized copying of configuration files is protected with PStore (Protected storage)
- Manual setting changes will require to provide the master password
- Password reset feature is introduced.
To Configure Master Password Settings
1. In the application menu, select Options.
2. Switch to the General tab.
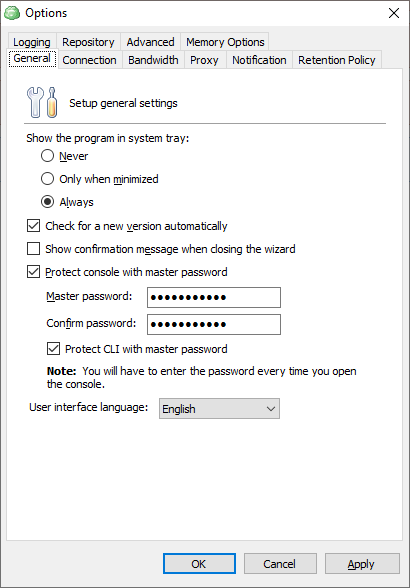
3. To specify the master password for accessing the application on each run, select the Protect console with master password check box.
4. Specify the password in the Master Password field, then in confirm in the Confirm password field.
5. To expand the master password protection for CLI usage, select Protect CLI with master password check box.
6. Click Apply.
Using Master Password in Command Line
Once a master password protection feature is expanded to CLI usage, you must use a master password to execute any CLI command.
To do it, use the -mp argument in any command.
To request the trial license under master password protection, use the following command:
cbb activateLicense -email "email" -edition "ultimate" -trial -mp [yourpass]where [yourpass] is a master password.
Reset Master Password
If you forgot your master password, you can reset it.
Once you run the Backup for Windows protected with a master password, in the dialog box, click Reset master password, then click Yes.
Note that once a master password is reset, all other passwords used in MSP360 Backup (for example, passwords for storage destination access), will be reset as well for security reasons.
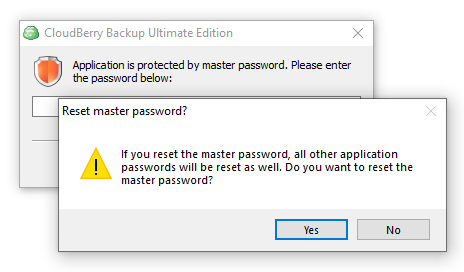
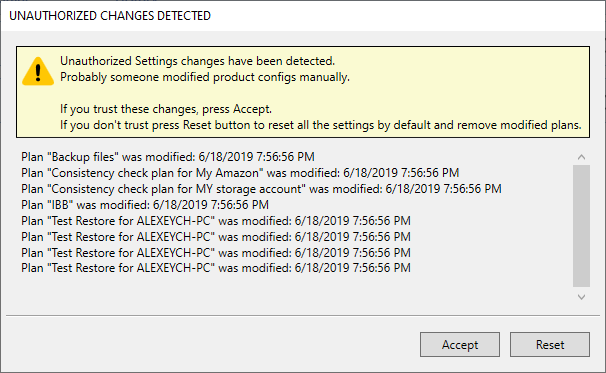
In case of setting modifications are detected, accept them or decline in the Unauthorized Changes Detected dialog box:
Top 5 SMB Pain Points Solved by MSPs
Small and medium businesses routinely don’t spend money on IT issues until there is a pain point that can no longer be avoided. They are focused on finding new customers, delivering services and keeping the lights on. For some, the world of software, servers, and networking is far from their comfort zone, or their interests. Continue reading
MSP360 Exibits at CompTIA ChannelCon in Las Vegas
Meet our team in Las Vegas, Nevada on August 5-7 for ChannelCon, the industry’s big event that connects leading solution providers, vendors, distributors, IT professionals, and media. Continue reading
5 Tips for Choosing Your Vertical
For many MSPs, it doesn't make sense to try to be all things to all people. Instead, MSPs often choose a certain vertical (or multiple verticals) to specialize in. For instance, an MSP might choose to focus on the automotive, healthcare or real estate industries, to name just a few example verticals. Continue reading
MSP Voice Episode 57 – “Residential and Commercial” with Nate Sheen
This week I am joined by Nate Sheen out of the greater Cleveland, OH area. Nate has owned his own MSP, DataCom Technologies, for over 4 years now and having great success by focusing both on residential and commercial customers. Continue reading
Introducing MSP360 Connect (Formerly Remote Desktop) 2.2
We are excited to announce new performance and usability improvements to MSP360 Connect, along with awesome new features, with the release of version 2.2.
CloudBerry Lab Becomes MSP360 Under New Leadership
CloudBerry Lab, the leading provider of multi-cloud data backup and recovery solutions, has announced rebranding under the new name MSP360 and the appointment of Brian Helwig as CEO. Continue reading
The Top Events and Conferences for MSPs
It goes without saying that a problem shared is a problem halved. Additionally, it’s been proven that two heads working together are better than one.
These, fundamentally, are the reasons why we persistently seek to learn from our peers and the MSP community at large. As a result, you get to expand your technical knowledge, as well as improve your overall service delivery and business development. Continue reading
MSP Voice Episode 56 – “MSP360 and Sales” with Brian Helwig
This week I’m happy to be joined by Brian Helwig, the CEO of MSP360 (formerly CloudBerry Lab). In case you haven’t heard, CloudBerry Lab is now MSP360. Brian and I previously worked together at Veeam where we had an office next to each other. When I heard Brian was joining MSP360 I was excited to work with him again. Continue reading
Think You’re Ready To Hire Your First Employee?
Running a one-man shop is stressful. You have to serve as head of sales, support, accounts payable and accounts receivable and more, all at once. And if the business runs solely on you, when you’re not working, you’re not making money. Even taking a sick day can set you back for the month. Continue reading
MSP360 at the ASCII SMB IT Summit
Thinking of attending ASCII SMB IT Success Summit in Denver on July 24-25? Well, guess what. MSP360 will be there as a sponsor and part of the vendor lineup. Meet David Gugick (VP Product Management) and Doug Hazelman (VP Technical Marketing, MSP Voice host) who will be representing MSP360 at the event. Continue reading