MSP Business
Core Managed Security Technologies and Software Any MSSP Needs
Whether you're a managed services provider (MSP) looking to transition into a managed security services provider (MSSP) or plan to launch a new MSSP business without having worked previously as an MSP, there are a variety of tools and you'll need to power your operations. This article offers a comprehensive overview of those tools, and the various types of MSSP service categories they cover.
(You might also want to read our Providing Managed Security Guide for a better understanding of the concept of managed security services.)
Categories of Managed Security Services
Before diving into specific types of MSSP tools, let's walk through the various categories of security services that an MSSP typically delivers. Understanding these categories is important for recognizing which tools will help you to address each one.
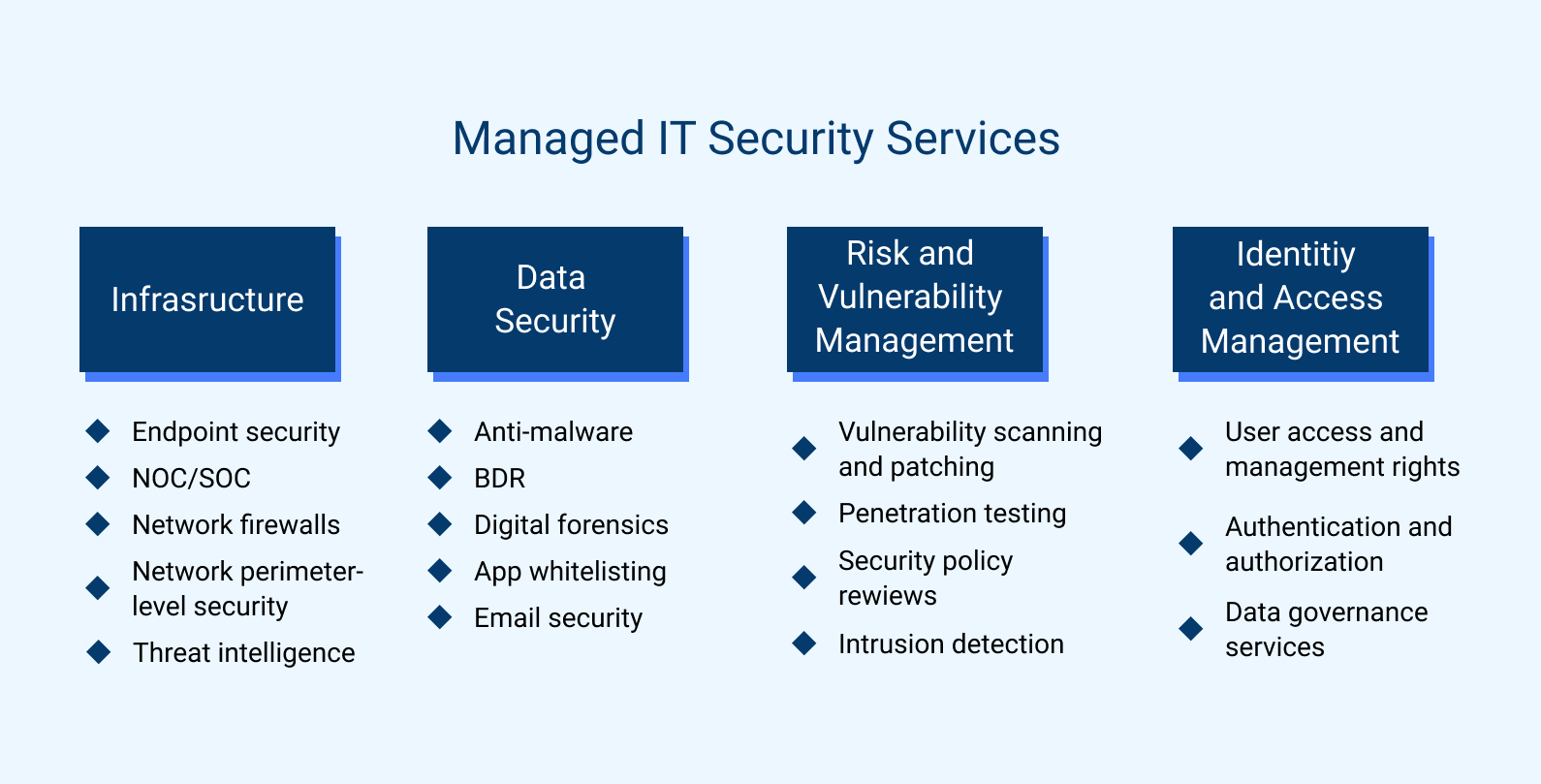
1. Infrastructure
First off are security services related to your clients' infrastructure. Here, an MSSP would typically offer the following types of services:
- Endpoint security: To protect individual devices that are connected to clients' network infrastructure.
- NOC/SOC services: Short for Network Operations Center or Security Operations Center, this type of service involves monitoring for and responding to all types of network and general security events.
- Network firewalls: To help prevent unauthorized access to your clients' internal networks.
- Network perimeter-level security: Along with firewalls, it helps to enforce a security boundary between internal and external network resources.
- Threat intelligence: To identify security threats and risks, and help prioritize different types of threats.
2. Data Security
MSSPs can offer several types of services to help protect data
- Anti-malware: To help identify and address malicious code within clients' systems, infrastructure, and applications.
- Backup and disaster recovery: Protects clients' data against the risk of loss due to security breaches and other disruptions. It also helps ensure that there is a "clean" version of data to restore if systems are compromised.
- Digital forensics: The discipline of investigating security incidents to determine what went wrong and prevent them from recurring.
- Application whitelisting and data-loss prevention: To help distinguish known-safe resources from potentially malicious ones.
- Email security: To mitigate the risk of phishing and other types of email-borne attacks.
Further reading Ultimate Data Security Checklist
3. Risk and Vulnerability Management
Finding and responding to different types of risks is another overarching service category for MSSPs. It includes:
- Vulnerability scanning and patching: Helps identify known vulnerabilities within applications and address them.
- Penetration testing: Simulates attacks that cybercriminals might perform to evaluate how well clients' infrastructure can withstand them.
- Security policy reviews: To identify misconfigurations that could lead to security vulnerabilities, as well as opportunities to make security policies even stronger.
- Intrusion detection: To monitor for and respond to intrusions and intrusion attempts.
Assess vulnerabilities and threats, network security, workspace and equipment security, documentation, and more. The pack includes:
- a ready-to-print PDF file
- an Excel file to help create a customizable assessment resource
4. Identity and Access Management
Finally, MSSPs typically provide services to set up and maintain access-control systems that help protect resources:
- User access and management rights: To establish permission-based policies that enforce who can access which resources.
- Authentication and authorization: To enforce permissions-based access to resources.
- Data governance services: Helps create best practices for managing an organization's data in a secure, reliable way.
Further reading Identity and Access Management in the Cloud
MSSP Software Stack
Now, let's take a look at which types of software tools help MSSPs provide the services described above. We won't get into specific MSSP tools or vendors since that is a separate issue, but we'll discuss categories of tools that should be in every MSSP's arsenal.
Further reading MSP Software and Hardware Tools
SOC (Security Operations Center)
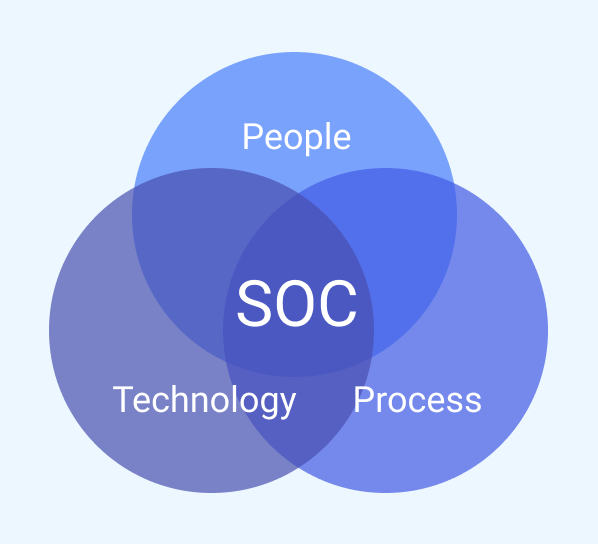 Particularly if you are transitioning from MSP to MSSP, it's often necessary to build out a full security operations center (SOC) to provide the level of proactive security monitoring and threat detection that businesses need.
Particularly if you are transitioning from MSP to MSSP, it's often necessary to build out a full security operations center (SOC) to provide the level of proactive security monitoring and threat detection that businesses need.
There are three components of SOC.
The human component. You need actual staff to power your SOC. At a bare minimum, you will likely need three positions:
-
- Security analyst/engineer: Provides monitoring for alarms and triaging threats that need to go to the incident responders. It also maintains tools and responds after a security incident is discovered.
- SOC Manager: Manages resources, staff, budgets, schedules and technology strategies to help the business meet agreed-upon customer service level agreements (SLAs).
- Security architect: Has expertise in both your security programs and the full security infrastructure of your MSP organization).
The technology component. You need to select the right SIEM tool (see below for more on this) to power your SIEM. Questions to consider while choosing a SIEM tool include:
-
- What do your customers’ environments look like? Are you dealing primarily with cloud, on-premise, or hybrid environments? Which types of operating systems are they using?
- Do your customers need to meet any compliance requirements? Some examples include HIPAA for healthcare organizations, PCI DSS for retail businesses, or SOC2 for cloud data service providers. Additionally, businesses that deal with data for European citizens will need to comply with the EU General Data Protection Regulation (GDPR), and those in the United States must address frameworks like the California Consumer Privacy Act (CCPA) and similar frameworks that are likely to appear in the coming years.
- What features or capabilities will your customers need? For example, will they need intrusion detection capabilities using the latest threat intelligence? Will they require rapid responses? If so, you may want a tool that can automate the incident response process.
The process component. Finally, you need the right processes in place to make your SOC work. Key guidelines to follow include:
-
- Build out repeatable processes, standard operating procedures (SOPs), and processes that make staff effective at their jobs.
- Work with your SOC manager to figure out how best to allocate resources (both budgetary and human).
- Your technology should support and enhance your workflow. Don't add MSSP tools to your workflow just because you can; make sure they address a specific need and don't unnecessarily duplicate functionality provided by other tools that you already use.
Security Information & Event Management (SIEM) Explained
 Security information and event management (SIEM) is another vital MSSP tool. SIEMs enable an approach to security management that combines SIM (security information management) and SEM (security event management) functions into one security management platform. The acronym SIEM is pronounced "sim" with a silent e (like the "sim" in "Simpsons").
Security information and event management (SIEM) is another vital MSSP tool. SIEMs enable an approach to security management that combines SIM (security information management) and SEM (security event management) functions into one security management platform. The acronym SIEM is pronounced "sim" with a silent e (like the "sim" in "Simpsons").
SIEM software integrates into the various security appliances in your client’s network to help you make sense of what’s going on. Data is acquired from the operation of your client’s network, and your SIEM will let you know which events you’ll need to pay attention to to keep your client’s network secure.
Client and server computers, intrusion detection and intrusion prevention devices, firewalls, routers, antivirus, and other components in your customer’s network should be generating event logs constantly. Those logs should be fed into your SIEM, were specifically configured correlation rules are used to determine if something happens that requires a human being's attention or intervention. Often, indications of a cyber attack receive a much quicker response when SIEM software provides a notification.
Antivirus Software
 Malware is one of the most significant types of security threats, and it can appear in many places -- within applications, in databases, as an email attachment, or even within an SMS. To address malware threats, MSSPs must provide an enterprise-grade antivirus solution for their clients that can detect malware no matter what form it takes or where it appears.
Malware is one of the most significant types of security threats, and it can appear in many places -- within applications, in databases, as an email attachment, or even within an SMS. To address malware threats, MSSPs must provide an enterprise-grade antivirus solution for their clients that can detect malware no matter what form it takes or where it appears.
Antivirus software will be running on your customers’ endpoints and servers, and possibly on some of their networking appliances as well (such as routers). Signatures and heuristics are deployed for malware detection. Popular enterprise antivirus providers include Cylance, Sophos, and Symantec.
Further reading Top Antivirus Solutions for Managed Service Providers
Endpoint Security Tools
 There are often multiple types of endpoint security tools that MSSPs may be expected to offer. They include antivirus interfaces for clients, event monitoring, vulnerability detection, and monitoring of network interfaces, among other functions. Some endpoint security tool vendors include Comodo, Sentinel One, and Cybereason.
There are often multiple types of endpoint security tools that MSSPs may be expected to offer. They include antivirus interfaces for clients, event monitoring, vulnerability detection, and monitoring of network interfaces, among other functions. Some endpoint security tool vendors include Comodo, Sentinel One, and Cybereason.
Further reading Endpoint Detection and Response (EDR) Explained
Backup and Disaster Recovery
 A client may need you to deploy a backup and disaster recovery (BDR) solution. A BDR solution includes different types of data backup systems, ensuring that if something like a cyber attack or natural disaster damages some of your client’s physical data storage, they have redundant data backed in a separate location (or, better, multiple locations).
A client may need you to deploy a backup and disaster recovery (BDR) solution. A BDR solution includes different types of data backup systems, ensuring that if something like a cyber attack or natural disaster damages some of your client’s physical data storage, they have redundant data backed in a separate location (or, better, multiple locations).
Further reading Backup and Disaster Recovery Explained
- Cross-platform backup and recovery
- Flexible licensing
- Bring-your-own storage approach


Network Firewall
 Firewalls allow you to filter traffic as it passes between a client's private network and the public Internet, between different segments of an internal network or between individual devices and the network. In the age of the cloud, where workloads often span across multiple devices and networks, firewalls are not as foolproof as they were when all workloads ran on-premises and could be neatly segmented behind a firewall. Today, it is often impossible to segment a workload off from the public Internet entirely. Still, firewalls remain a useful tool for adding another layer of protection to clients' networks.
Firewalls allow you to filter traffic as it passes between a client's private network and the public Internet, between different segments of an internal network or between individual devices and the network. In the age of the cloud, where workloads often span across multiple devices and networks, firewalls are not as foolproof as they were when all workloads ran on-premises and could be neatly segmented behind a firewall. Today, it is often impossible to segment a workload off from the public Internet entirely. Still, firewalls remain a useful tool for adding another layer of protection to clients' networks.
Further reading Network Security Best Practices
Threat Intelligence Software
 Threat intelligence software provides notifications about vulnerabilities, malware, and attack techniques are they are announced and discovered. It helps MSSPs stay up-to-date with the latest threats that their clients face, as well as understand which threats apply to the clients they support.
Threat intelligence software provides notifications about vulnerabilities, malware, and attack techniques are they are announced and discovered. It helps MSSPs stay up-to-date with the latest threats that their clients face, as well as understand which threats apply to the clients they support.
Email Firewall
 Email is vital to the business, including that of your MSSP clients. You might have to deploy email firewalls to keep those vital systems safe from cyber attacks. Some email firewall vendors include Cisco, McAfee, and Fortinet. If you are looking for a secure email firewall tool, you may also find our email firewall comparison article helpful.
Email is vital to the business, including that of your MSSP clients. You might have to deploy email firewalls to keep those vital systems safe from cyber attacks. Some email firewall vendors include Cisco, McAfee, and Fortinet. If you are looking for a secure email firewall tool, you may also find our email firewall comparison article helpful.
Further reading The Comparison of Email Firewalls for MSPs
Password Management Tools
 Insecure passwords are a major vulnerability that cyber attackers can exploit to acquire unauthorized access to computer systems. MSSPs therefore often provide clients with a password management solution to ensure that stronger passwords are used for better security. Some popular password managers are 1Password, Centrify, and Dashlane.
Insecure passwords are a major vulnerability that cyber attackers can exploit to acquire unauthorized access to computer systems. MSSPs therefore often provide clients with a password management solution to ensure that stronger passwords are used for better security. Some popular password managers are 1Password, Centrify, and Dashlane.
Further reading Password Management Best Practices
Application Whitelisting Tools
 Application whitelisting can complement an antivirus solution by assuring that only authorized software can be used in your client’s network. Applications that aren’t whitelisted might be malicious. Some application whitelisting vendors include Airlock, Bitdefender, and Lumension.
Application whitelisting can complement an antivirus solution by assuring that only authorized software can be used in your client’s network. Applications that aren’t whitelisted might be malicious. Some application whitelisting vendors include Airlock, Bitdefender, and Lumension.
MSP Software
 MSP software is a whole category of tools unto itself, ranging in functionality from remote monitoring and management tools (RMM), professional services automation (PSA), account management, asset management, backup and patching automation, and beyond. Even if you're an MSSP and not an MSP, having MSP tools in your arsenal will help you access, manage, and monitor clients' systems in ways that reinforce your security operations. Some popular MSP software vendors include SolarWinds and ManageEngine, among others.
MSP software is a whole category of tools unto itself, ranging in functionality from remote monitoring and management tools (RMM), professional services automation (PSA), account management, asset management, backup and patching automation, and beyond. Even if you're an MSSP and not an MSP, having MSP tools in your arsenal will help you access, manage, and monitor clients' systems in ways that reinforce your security operations. Some popular MSP software vendors include SolarWinds and ManageEngine, among others.
Further reading MSP: Do You Need RMM, PSA, or Both?
Conclusion
Although each MSSP is free to determine which specific types of services it wishes to offer, MSSPs typically provide an array of managed security services that cover areas ranging from data and infrastructure security to risk management and vulnerability detection. Success as an MSSP starts with determining which services you intend to provide, then finding the MSSP tools that will allow you to deliver each of those services effectively and cost-efficiently.




