There’s nothing new or especially significant about the remote work concept. Students and employees have been doing it in increasing numbers over the past decade. What changed the game was the recent immediate mass exodus from workplaces and classrooms to home offices or even the living room table as a result of the COVID-19 pandemic.
While it seems an easy enough matter simply to change the location from which you work and continue on your way, the suddenness with which this recent societal upheaval was thrust upon companies left little time to prepare the necessary cybersecurity processes and protocols properly.
And if there is one thing hackers have taught us in recent years, it’s that if there is a weakness, they will find it.
Thanks to the generalized fear and panic surrounding COVID-19, those inclined to do so have found it a relatively simple matter to take advantage of the at-home workforce who are not schooled in protecting the device they’re working on against common threats.
How can an organization ramp up its efforts to protect sensitive information? We have some ideas.
Read this free whitepaper to learn more about:
- How to move your operations out of the office;
- Security considerations for remote workers;
- Best practices and tools;
- And a lot more.
COVID-Themed Attacks
The current wave of attacks plays off a remote worker’s fear of the thing that sent them home in the first place, namely, the pandemic. There has been a deluge of fake emails pretending to come from the World Health Organization, with appropriately fear-inducing wording intended to encourage a click that will download malware on to your laptop. Another tactic is to take the identity of a charity organization and go for the click that way.
Further reading Coronavirus Phishing
The bottom line is that people are stressed over the pandemic, not as focused as they should be, and likely to forget the company security training from six months ago on how to recognize and prevent social engineering attempts like phishing.
A single wrong click of the mouse and you’ve got malware. And email is no longer the typical avenue of ingress. “Smishing” - a form of social engineering aimed at SMBs who use business-to-business SMS messaging to stay connected - has seen a steady rise in popularity. Malicious links can be transmitted that way as well, so consider yourself warned.
Even worse, if you’re remotely connected to company resources at the time, you just offered Mr. or Mrs. Hacker a nice, clear shot at taking down the network or at least accessing any confidential data that might be there.
Obviously, companies are concerned about the prospect of a workforce operating outside the secure environment they are used to. Here’s how the smart ones are responding.


Bolstering Remote Security - Key Solutions
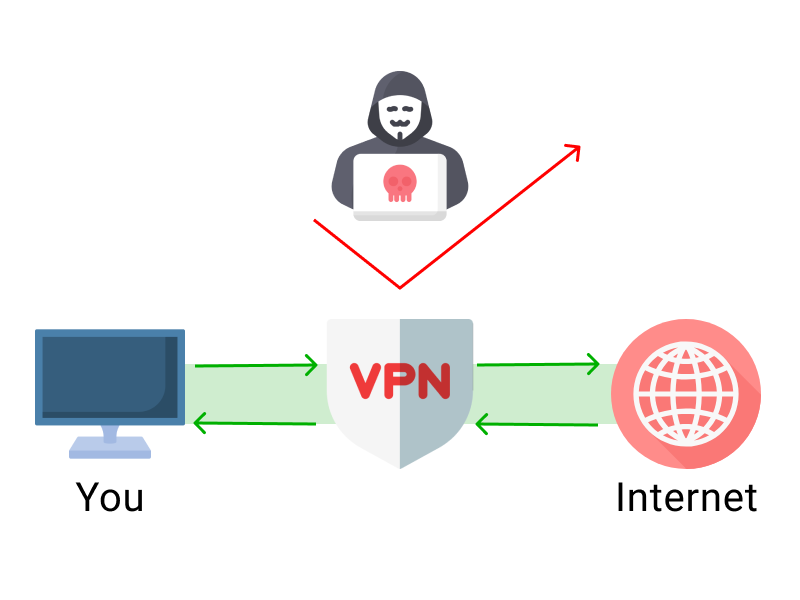
Remember that secure environment we just mentioned? Likely it included an enterprise VPN to encrypt data flow and redirect IP addresses to protect connections accessing the open Internet. Now, the same enterprise VPN protocols are available through most leading consumer VPNs. There’s also a good chance that on-premises security also included a firewall, an antivirus security suite, anti-malware software, and monitoring tools to prevent, locate, and mitigate security threats.
But with a suddenly remote force, the IT department has lost control of the carefully constructed and secure environment. From its perspective, every remote employee is now an additional threat vector. To put it mildly, they’re feeling uncomfortable.
Reinforce Social Engineering Training
Every employee needs an immediate refresher course on how to avoid phishing traps. It’s a simple education, though harder to follow exactly, due to human nature. The bottom-line requirement is to never click a link in an email or open an attachment unless you know exactly who it came from and were expecting it. See? Easy to comprehend but harder to execute flawlessly, and all it takes is a single lapse to take down an entire network.
Further reading Anti-Phishing Training
Like the smishing mentioned earlier, social engineering attacks can come from unexpected directions. Some employees are learning new processes for getting paid as a result of working off-site. Was that invoice template downloaded from a legitimate source? If not, be careful. File formats like PDF and documents that were once considered unhackable actually aren’t.
Prioritize Operations
Companies need to lock their remote force down and do it fast. Meet with the company decision-makers and establish which parts of the operation are mission-critical and which can be put on the back burner. Focus on the former, and only after they are secured is it time to proceed to the rest.
Review Remote Security Status
Then it’s a good idea to assess each employee’s work device (laptop or desktop) and evaluate its security level and threat vulnerabilities. In a perfect world, the company would be able to send each team member home with a device that had already been fortified. Not every organization was ready to do that when COVID-19 hit, so much of the remote force is tending to their daily business with largely unsecured home machines.
There’s a good chance the company will find itself in the position of having to buy a whole lot more licenses for security products in order to replicate that secure environment in dozens, hundreds, or thousands of remote locations. And then you have to worry that people don’t know how to install them properly or at all. The IT staff might be forced into making home visits in order to verify security, though the whole social distancing aspect of the pandemic complicates that task as well.
Final Thoughts
Smart employers now have a two-fold mission to protect their remote workforce from COVID-19 on a couple of different fronts. First, of course, is to encourage them to follow local, state, and federal guidelines on how to reduce the chances of contracting the dread disease. Stay home as much as possible. Social-distance when you have to go out. Wear masks.
But then there is also the necessity of maintaining a high alert against those who use the specter of COVID-19 to boost their chances of a successful hack. Companies that suffer compromised networks sometimes end up going out of business. Nobody wants that, so everybody should take security seriously these days.









