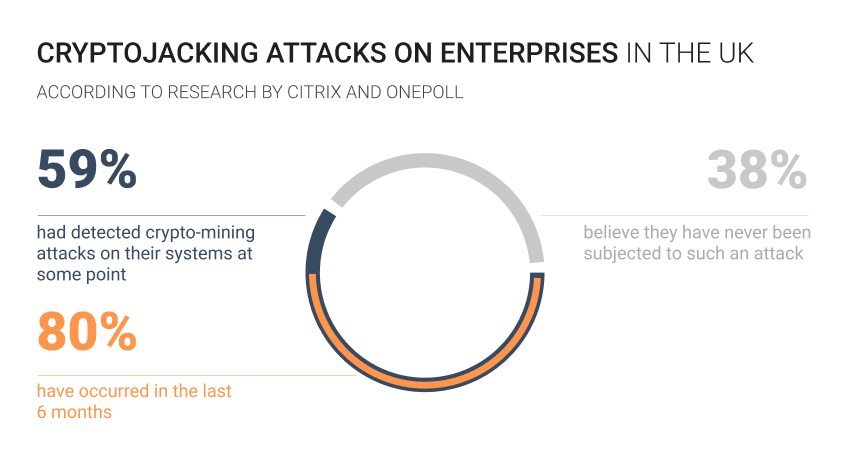
Modern hackers now look to take advantage of the mining boom by building malware that can hijack one or more systems and remotely use the hardware for financial gain. Such attacks are known as cryptojacking and continue to affect more and more internet users.
Trends in cybercrime tend to be dictated by financial factors and nowhere is that more evident than with the rise of cryptocurrency mining malware.
Hackers and digital currencies like Bitcoin and Ethereum go together like peas and carrots (to paraphrase Forrest Gump), due to the fact that there is no central bank and transactions can be anonymous.
If you’re wondering whether or not Bitcoin is a serious financial player, it is. This most popular cryptocurrency has a market cap of about $114 billion.
Cryptocurrencies are built on a technology known as blockchain, where a network of distributed nodes run complex algorithms to determine the next secure sequence for a digital transaction. This process is known as mining, and with enough computing power, any individual can earn cryptocurrency credit from a personal computer.
Characteristics of Cryptojacking
So what is the financial incentive with cryptojacking that makes it more appealing to hackers than other forms of cybercrime? The key is the continuous nature of the attack and the fact that the person who's been targeted may not detect the problem for a long time.
Running software that mines cryptocurrency requires high-end computers with expensive graphics cards, as well as a great deal of electricity to keep the algorithm computations happening around the clock. Most experts agree that it costs a person more money to run their own mining computer than they can actually earn in Bitcoin or Ethereum.
The allure of cryptojacking is that the hackers do not need to pay for computing power or electricity but can still reap the rewards of mining. When such an attack is executed, a piece of background software is installed unknowingly that runs the algorithm processes and directs all earnings to the hacker's cryptocurrency wallet.
Hackers also design their cryptojacking malware to spread from computer to computer on a local network, which means they can compromise a serious amount of computing power and bring in a consistent income from digital currencies. Other types of hacks, like ransomware, are typically one-off transactions that cannot be repeated.
Injection of Mining Malware

When a hacker plans a cryptojacking attack, their first challenge is to get the malware installed on the remote computer. This is typically done one of two ways: by gaining administrative access to the operating system or by tricking the primary user into installing the virus themselves.
Many cryptojacking hacks begin with spear phishing, which is where personalized spam email is sent out to an individual and urges them to click on a link or respond with personal information. These types of messages often imitate a legitimate company and claim there is an account issue or error. Organizations without spear phishing prevention tools are extra vulnerable to cryptojacking attacks.
Sometimes cryptojacking malware can be installed through a compromised router on a public wi-fi router. Hackers redirect traffic from a computer to try to obtain the administrative password. If successful, the cryptojacking attack proceeds by launching as a background process.
The best tactic for avoiding this type of infiltration is to use a strong virtual private network (VPN) service when browsing on public wi-fi networks. The downside to this is that some countries, the usual suspects, have banned the use of VPNs. If this is the case for you, there are alternate methods of connecting to the internet that can hide your IP address from potential hackers.
Detecting a Cryptojacking Attack
Hackers who specialize in cryptojacking schemes have become increasingly clever in making their malware difficult to track or detect. Computer users may not see any suspicious processes listed in their Task Manager because the malware is either hidden or else named with a deceiving label that makes it look trustworthy.
For individual users, the best way to watch for potential cryptojacking attacks is to monitor the performance of their computer. Mining malware requires a great deal of CPU power, often over 90 percent, which will cause the rest of the system to grind to a halt. If you notice that applications are suddenly running significantly slower on your computer, even after a full reboot, then there is a chance your system is infected with cryptojacking malware.
Believe it or not, another good way to detect cryptojacking is by checking the physical temperature of your desktop or laptop computer. The increased CPU usage will result in more heat within the hardware, causing your system to either crash or run its internal fans constantly when no applications seem to be running.
Removing Malware
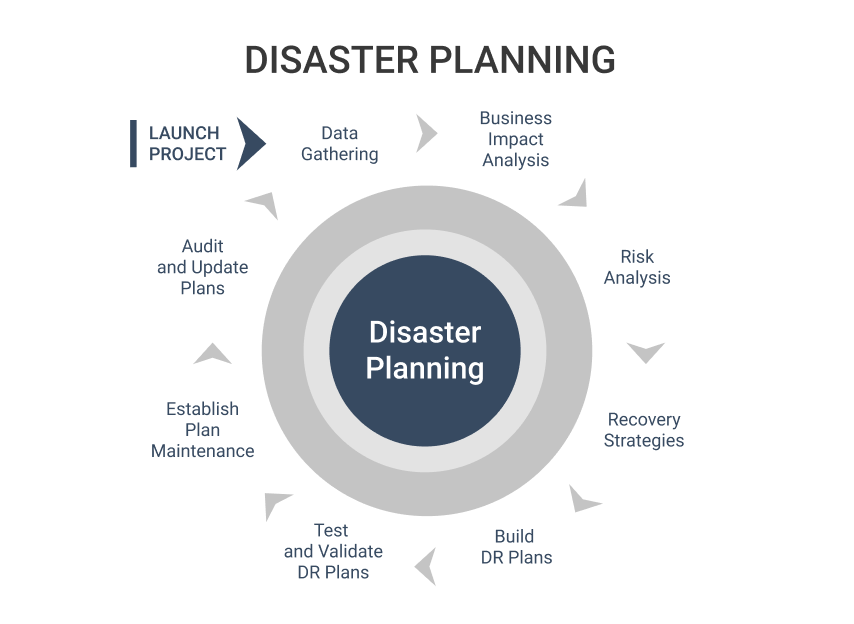
After cryptojacking has been detected in an organization, the IT team must engage their disaster recovery plan. The first action item should be to disconnect the affected hardware from the internet to halt the mining activity and avoid the spreading of the malware to more machines. Then the focus can shift to removing the actual virus.
Some cryptojacking attacks are executed through web browsers, so part of the removal process is to disable and uninstall any extensions or add-ons being used with Google Chrome, Mozilla Firefox, or other browsers.
Next, a strong malware scanner should be installed on the affected hardware with the latest updated virus definition files. This type of tool can scan all system and registry files to identify the root of the malware and clear it from the hard drive.
If the mining malware cannot be completely removed from a computer, you can still salvage the hardware by reverting to a backup snapshot that was captured before the attack began.
The Bottom Line
If there is one thing to remember, it’s the absolutely critical importance of full backups that are stored offsite. Once cryptojacking malware has burrowed into your system, the only real solution might be to wipe the drive and re-install a backup copy. If you have a backup that is
If you don’t have a backup - umm - get one as soon as you can. Even better if it’s stored in the cloud. Good luck out there because if the cryptojackers haven’t found you yet it’s not because they’re not trying.